Weave Security into the Fabric of the SDLC
Shift security left to identify and remediate vulnerabilities and defects early in the process.
Certify open-source components and supply chain software in a sandbox environment before moving into production.
Protect workloads in production against zero-day vulnerabilities and block threat actors in real-time.
With Dev-Native Security,
your applications and workloads are:
Shift Left with continuous automated security integrated with your SDLC to detect and mitigate vulnerabilities early.
Continuously verify apps with automated "Build-over–Build" code path discovery and policy, risk, and vulnerability testing.
Bubble-wrap applications and workloads with “Protect until Patched” policies and detect and mitigate runtime attacks in real-time.
Automate security across the SDLC to secure custom code and ensure the integrity of 3rd party and open-source software.
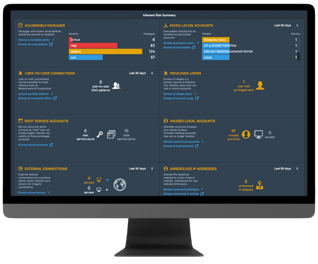
AppSec Challenges
Today's application and API security is too slow, complex, and costly.
App Vulnerabilities
Open Source Attacks
Fix in Production
Prismo Dev-Native Security
Implement DevSecOps for enterprise applications, infrastructure, and data by weaving security into the very fabric of the SDLC for complete end-to-end application security, workload protection, and compliance automation.
- Protect custom code and the supply chain
- Automate security across the entire SDLC
- Protect applications at run time in production
- Automate Pen Testing and Vulnerability Management
- Comply fully with best practice and regulatory frameworks
Prismo Dev-Native Security
Implement DevSecOps for enterprise applications, infrastructure, and data by weaving security into the very fabric of the SDLC for complete end-to-end application security, workload protection, and compliance automation.
- Protect custom code and the supply chain
- Automate security across the entire SDLC
- Protect applications at run time in production
- Automate Pen Testing and Vulnerability Management
- Achieve Full OWASP Compliance
Dev-Native Security Use Cases
- Secure Development
- Workload Protection
- Compliance Assurance
Secure your code across every
stage of the SDLC
AppSec Challenges:
- Speed: With release velocity increasing, manual testing and snapshots in time don't work and security can't keep up with DevOps
- Complexity: Too many siloed tools creates complexity and hinders security automation
- Cost: The cost to fix in production is 100x that of fixing in design
How Prismo Helps:
- End-to-End Automation: Continuous, agile, cross-platform approach is fully integrated with DevOps and SDLC tools
- Shifts Security Left to identify and remediate vulnerabilities early
- Lowers TCO by automating testing, discovering and remediating vulnerabilities earlier, and enabling security stack consolidation by unifying many security functions under a single platform
Protect workloads from advanced attacks with 360° workload segmentation
Workload Protection Challenges:
- Open-Source and commercial software are susceptible to backdoors and vulnerabilities making the enterprise vulnerable to supply chain and ransomware attacks
- Lateral Movement is hard to prevent and detect leading to long dwell times and hidden risk
- Advanced threats like ransomware and supply chain cannot be prevented with endpoint and network micro-segmentation solutions alone
How Prismo Helps:
- Zero-Touch Whitelisting of executables, libraries, and scripts enables blocking of ransomware at install eliminating dwell time and reducing risk
- Prismo's 360° workload segmentation stops lateral movement by enforcing segmentation of apps, domains, users, and services while automation reduces human effort and errors
- ML-based app fingerprinting certifies supply chain software and enforces approved behavior of certified applications
Achieve true risk-centric security
and compliance
Compliance Challenges:
- Increasing regulatory obligations and compliance reporting requirements
- Manual, spreadsheet-based GRC approaches are time-consuming, inefficient, and unsustainable as organizations move to the cloud
- Without continuous monitoring, audits are snapshots in time providing no real-time view of risk and compliance
How Prismo Helps:
- Automated mapping to NIST CSF and ZTA, MITRE ATT@ck, OWASP, and other standards provides a future-proof solution for evolving compliance requirements
- Automated vulnerability management and audit and compliance reporting reduce human effort, errors, and costs
- Continuous monitoring and policy-driven enforcement and reporting enable real-time visibility of risk and compliance
What challenges do you need to solve?
Prismo's unique Dev-Native approach enables automated security and compliance across the entire SDLC
App and API Security
Weave security into the fabric of your SDLC from development to deployment, protecting apps from code to cloudSupply Chain Integrity
Protect against supply chain attacks from 3rd-party software, open source libraries, and back doorsWorkload Protection
Enforce Zero Trust-based workload segmentation at the granularity of every resourceSecure Code
Prismo integrates security across your entire SDLC, from code to build, and at runtime
Prismo’s full-cycle DevSecOps solution provides end-to-end security and automation from dev to production.
- Custom Apps and APIs: Supports full-cycle DevSecOps with automated discovery and testing.
- VM and Container Builds: Includes intent-based policies to protect against backdoors and real-time mitigation for active threats.
- 3rd party and Open Source modules: Tests in a cloud-native sandbox to uncover vulnerabilities.
Protect Workloads
Prismo secures workloads against advanced supply chain and ransomware attacks<br>across the entire lifecycle - from code to runtime
Assure Compliance
Leverage and comply with industry and government frameworks and standards
Out-of-the-Box Integrations










Partners
We partner with top technology platform providers, security vendors, and channel partners to enable customers quickly realize the benefits of adopting a Dev-Native approach to security.




Partners
Prismo partners with platform providers, security vendors, managed service providers, and global systems integrators to deliver on the promise and benefits of Active Cyber Risk Management.




Customers Agree
Accelerate market adoption via leveraging 3rd party applications and Open Source modules.
Challenge: Ensure that 3rd party applications are trustworthy.
Solution / Capabilities:
- Discovers every system and executable
- Maps, fingerprints at process and service level, and whitelists executables
- Shows security issues, flaws that are vulnerabilities, processes not used, spurned by infrastructure, active at shutdown, and more.
- Protects against backdoors and other security issues in production.
Business Result(s):
Knowing that 3rd party / Open Source components are trustworthy enables them to accelerate development and more confidently tackle new markets.





