
Prismo Security Platform
Cloud-Native
Application Protection
A new holistic end-to-end approach to enterprise security
Single platform for application scanning, workload protection, and cloud security posture management
A purpose-built security data lake lowers TCO and ensures your growth won't outpace your security
Meets and exceeds all NIST Zero Trust Architecture (ZTA) standards, providing a clear path and gateway for ZTA adoption
 Dynamic Risk Modeling
Dynamic Risk Modeling
Provides a real-time, continuous, and cumulative risk assessment of every enterprise entity and resource
Defeats today’s sophisticated supply chain and ransomware attacks with automated real-time mitigation
Transaction Graph Data Lake
At the core of our solutions is The Prismo Security Platform and its patented Transaction Graph architecture.
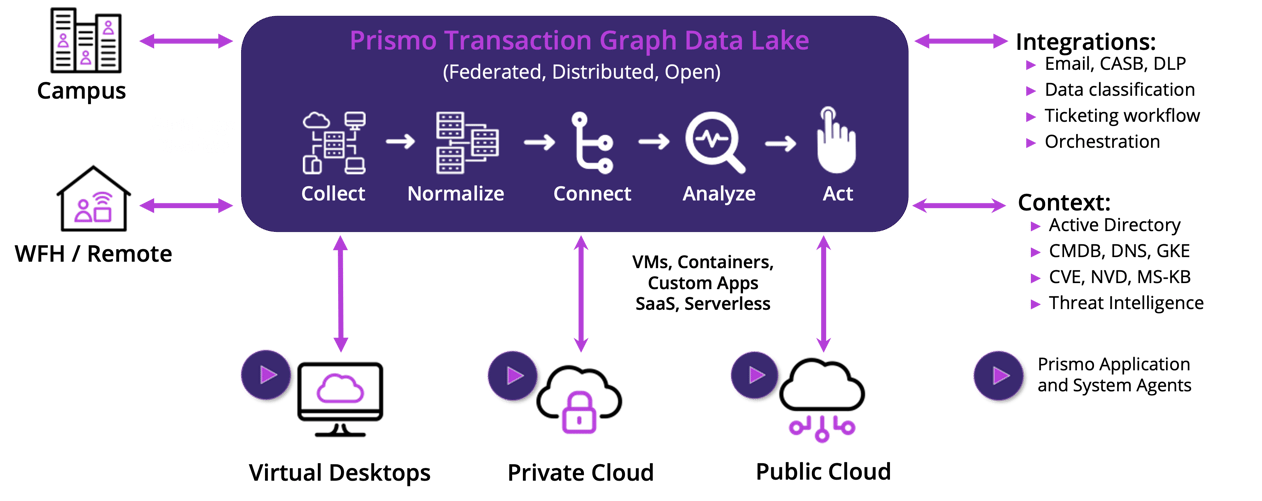
The Prismo Platform provides a unified, cloud-native, and open approach to security and compliance for
custom code, supply chain software, and workloads across hybrid cloud environments.
The platform is fully compliant with NIST 800-207 Zero Trust architecture.
Built for Zero Trust
The Prismo Platform enforces Zero Trust policies in real-time and provides continuous 360° risk assessment
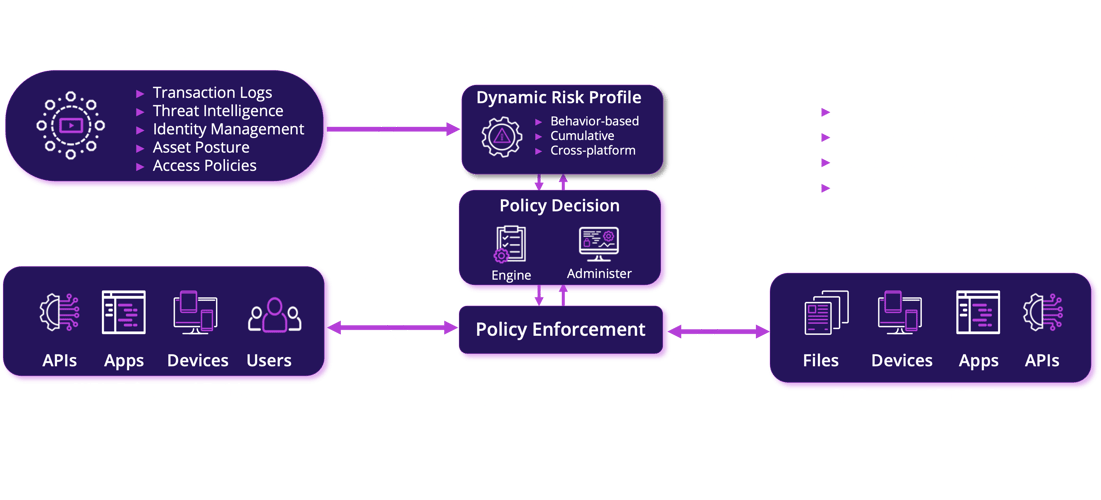
The Prismo Platform enforces Zero Trust policies in real-time and meets or exceeds all NIST ZTA guidelines.
Its unique Dynamic Risk Profile provides a unified, continuous, event-driven assessment of risk
for all entities and resources across the entire enterprise IT environment.
Dynamic Risk Modeling
Real-time, continuous, and cumulative risk assessment of every entity and resource
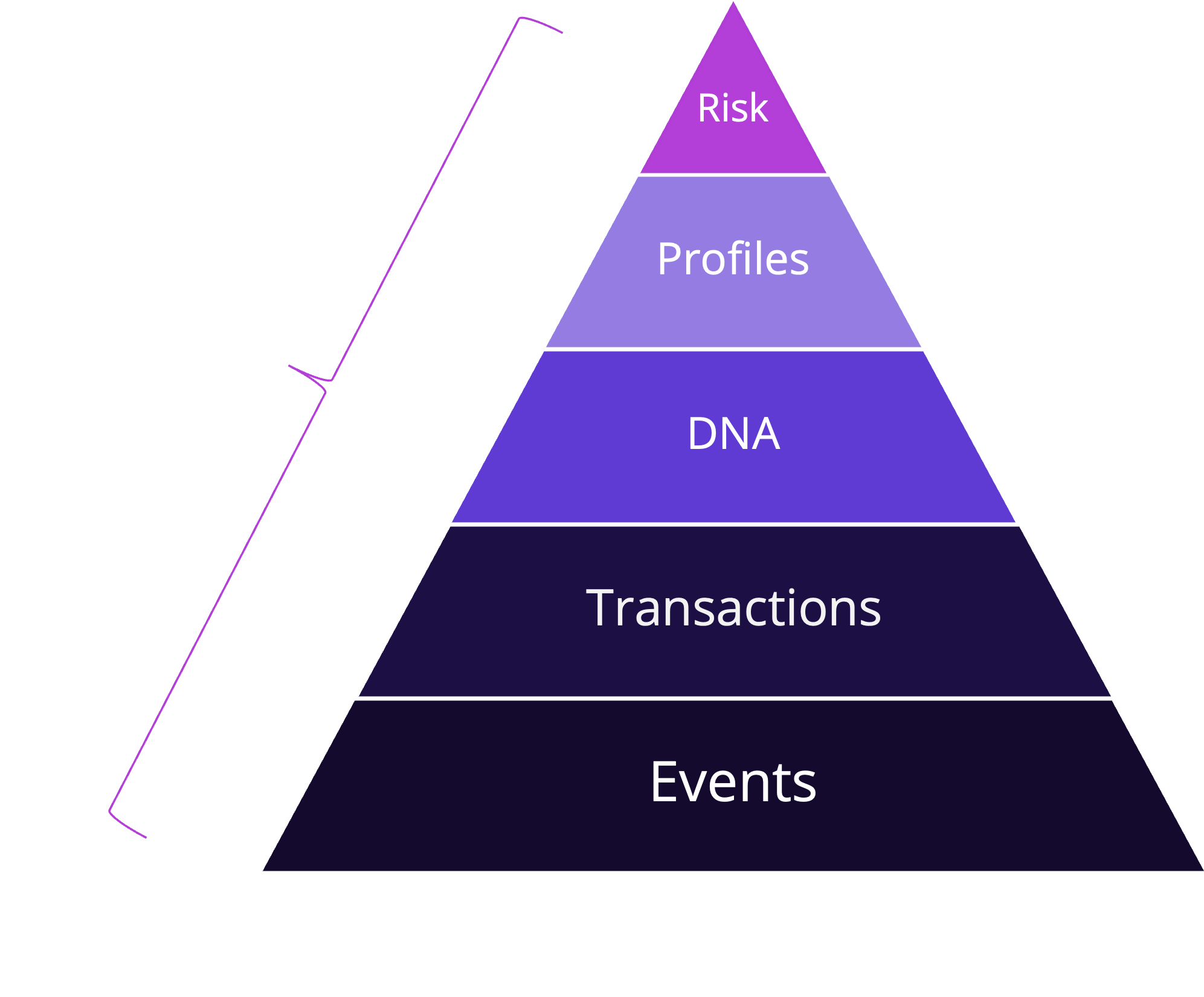
The Prismo data model processes trillions of discrete events and step by step transforms the data into a small pool of highly targeted, highly relevant, risks. A Dynamic Risk Profile is used to evaluate subtle compromises to discrete systems over time enabling detection of stealthy,"low and slow" attacks, such as Supply Chain and ransomware. This process encompasses:
- Data Model: The Prismo data model condenses trillions of uncorrelated events into a small pool of specific, relevant actions and a Risk Profile per entity.
- Threat Frameworks: Threat frameworks such as OWASP, NIST, and MITRE provide critical detection and mitigation guidance.
- Active Mitigation: Once the cumulative risk has passed its threshold, even over a long period of time, mitigation is executed automatically and in real time.
Real-time Automated Mitigation
Active mitigations prevent even successful compromises from escalating to breach
A successful compromise can lead to lateral movement and escalate to a full blown ransomware attack or breach quickly. To counter fast-moving attacks, mitigations must be active and automated. Prismo detects and actively mitigates threats, even successful compromises, before they can escalate to a breach.
- Continuous Enforcement: Prismo meets or exceeds NIST Zero Trust Architecture guidelines with continuous event-level authorization and enforcement rather than session or transaction-based authentication.
- Intelligent Policies: Prismo automates the creation of intent-based policies to prevent rule conflicts and gaps from allowing a compromise
- Active Mitigation: Prismo actively enforces policies and mitigates risks in real time.
360° Visibility and Context
Prismo connects your siloed data in real-time to eliminate blind spots and provide 360° visibility and context
The Prismo Platform connects data silos in real-time by connecting and linking interactions between Sources and Resources, enriching them with external context, and transforming them into complete end-to-end transactions to provide unprecedented risk visibility, contextual insights, and security control.
- Connect: The platform connects events and data across silos from sources to resources eliminating blind spots.
- Enrich: Rich 360° context is added to each transaction which are then linked into tasks creating a rich analysis baseline.
- Analyzes: Multi-dimensional fingerprinting combined with baseline analysis creates Chains-of-Trust.
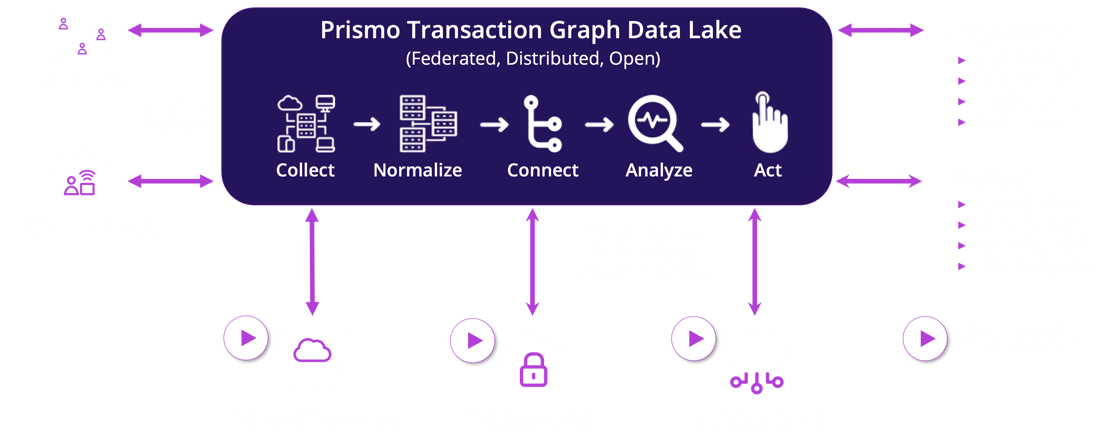
Unified, Open, and Integrated
Prismo's open architecture integrates with CI/CD, cloud, security, and other platforms
with API access at every level of the data stack.

Prismo’s Zero Trust Platform provides continuous authorization and response with event-level granularity:
- Open: Architecture provides full API access across the every level of the data stack to integrate with custom systems and data
- Extensible: Full SDK access enables customers to extend the platform with custom functionality
- Integrated: Out-of-the-box integrations with top technology and cloud platforms, security solutions, authentication systems, and more, enable rapid deployment and time to value
Out-of-the-Box Integrations










