By Abhishek Singh and Ramesh Mani
Web injection exploitation has ruled as the top web application vulnerability for a decade. “Security Vulnerabilities in Network Accessible Services” report was published by Independent Security Evaluators ISE[1]. As per the report, 13 IoT devices evaluated by ISE had at least one web application vulnerabilities such as cross-site scripting (XSS), operating system command injection (OS CMDi), or SQL injection (SQLi) that could be leveraged by an attacker to get remote access to the device’s shell or gain access to the device’s administrative panel. OS command injection is an exploitation technique in which the goal is the execution of arbitrary commands on the host operating system via a vulnerable application. OS command injection exploitation is operating system-independent; i.e., it can happen on Windows or Linux. At the Virus Bulletin 2019 conference, we shared the details of the parameter integrity algorithm to detect OS command injection. In this blog, we present the same details of the parameter integrity algorithm along with the detection efficacy to detect the publicly available exploits. Finally, we conclude by introducing the concept of detect, response, and remediate. If the detection algorithm/technology follows the principle of detect, response, and remediates, then with each detected attempt of exploitation, if remedial action is taken, it will increase the exploitation complexity for threat actors to breach an organization.
Technical Details of OS Command Injection
Figure 1.0 shows the code vulnerable to OS Command Injection attack.
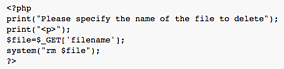
Figure 1.0 Code Vulnerable to OS Command Injection Exploit. The code takes the name of the file which is to be deleted from the value field of the method GET. In the subsequent line of code PHP program execution function system(), takes the value of the file name from the data field of GET method and invokes the bash command “rm” to delete the file. Let's assume that the file shown in figure 1.0 is on the server with IP address x.x.x.x as test.php. “hxxp://x.x.x.x:8000/test.php?filename=kral.php” is an example of the legitimate input. It takes in input as “kral.php” from the data field of the GET and deletes the file “kral.php” from the folder. The dynamic call graph which captures the execution flow i.e. control and data dependency is shown in figure 2.0. This dynamic call graph captures the control and data flow not only when the code is executed by a PHP application but also when the OS commands are executed by the PHP application. The nodes in the graph denote the statement, predicates, OS events, and system calls. The edges denote the parent-child relationship.
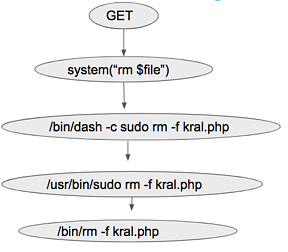
Figure 2.0 Dynamic Call Graph of the legitimate request. “http://x.x.x.x:8000/test.php?filename=kral.php;ls” is an example of an OS command injection exploit. In the request, the threat actor has injected the OS command “ls” with the value of the GET method “kral.php”.
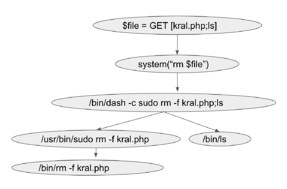
Figure 3.0 Dynamic Call graph having OS Command Injection Exploit. Figure 3.0 shows the dynamic call graph when the exploit is sent to the vulnerable application. As can be seen, a new node having the value “/bin/ls”, the injected OS command, is spawned. The value of the additional node can be traced up the graph and is the same as the command “ls” to the value field of the GET method. The command “ls” is separated by the delimiter “;”. Besides “;” the other delimiters which can be used to inject OS command in Linux and WIndows environment are “|”,”;”,”&”,”$”,”>”,”<”,””,”!”.
Detection of OS Command Injection
The parameter integrity algorithm to detect the OS command injection exploitation not only makes use of the application-level hooking to capture the API’s invoked by an application in Python, PHP, JAVA but also captures system calls and other OS events reported by the kernel driver to generate the dynamic call graph. The dynamic call graph traces the data and control passed to the methods that accept user or external inputs such as GET, POST, Cookies, HTTP Headers etc. to the program execution function. The dynamic call graph also traces the subsequent child processes which can be OS events or invocation of the system calls spawned due to the execution of a program execution function (such as eval(), passthru(), shell_exec(), system(), proc_open(), expect_open() or ssh2_exec() for PHP applications or OS.popen2(), os.popen(), subprocess.call(), os.system(), subprocess.Popen(), eval(),exec() for python applications). Once the dynamic call graph has been generated, during every invocation of the program execution functions, the parameter integrity algorithm will use the graph to check, whether the exact name of the command line argument of any of the child process of the program execution functions that are being spawned by the OS command is same as the value or appears in the part of the value passed to the methods that accepts user inputs such as GET, POST, Cookies & HTTP headers. If the condition is found to be true, an alert of OS command injection vulnerability is raised.
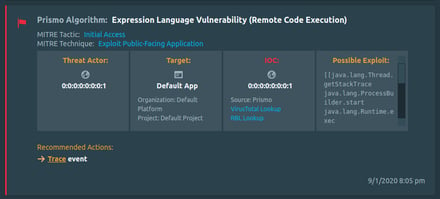
Figure 4.0 Detection of OS Command. The algorithm identifies the injection vulnerability in the code during the invocation of the program execution functions. With each detected exploitation attempt, the vulnerable code path also gets detected. This automatic identification of the vulnerable part of the code will aid to patch the code preventing further exploitation.
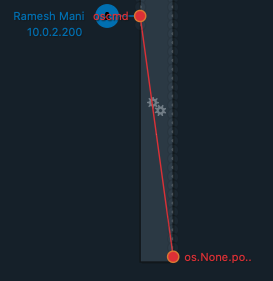
Figure 5.0 Vulnerable code path in application Parameter Integrity algorithm to detect OS command injection was tested against the publicly available exploits. The algorithm successfully detects variation of OS command injection exploits. Further details of detection efficacy is available here.
Conclusion
Currently, a majority of the detection technologies and algorithms follow the principles of detection and response. In the detection and response model, once exploitation gets detected by using behavioral, machine learning algorithms, scanning packets, using signatures, deception etc., the next step is to immediately respond by stopping the threat by dropping network connection, blocking IP, suspending or killing processes, quarantining files etc. The parameter integrity algorithm discussed in this blog and the query integrity algorithm detailed in the previous blog follows the principle of detect, response, and remediate. Not only does the algorithm detect exploitation, but responsive measures can be applied to stop exploitation. It also provides remedial action, which taken will increase the exploitation complexity for a threat actor. In the case of parameter & query integrity algorithm, remedial action is patching the vulnerable code path, which automatically gets identified with each detected attempt of exploitation. If the code gets patched, detection alerts will decrease, increasing the exploitation complexity for a threat actor.
References
[1] Security Vulnerabilities in Network Accessible Services, https://www.ise.io/casestudies/sohopelessly-broken-2-0
