By Abhishek Singh and Ramesh Mani
Web application vulnerability remains one of the critical entry vectors which have been employed by threat actors. Injection vulnerability has been ruled as one of the critical vulnerabilities in OWASP top 10 [2]. MITRE ATT&CK™, which is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations, also lists Injection based exploitation as one the entry vector for threat actors under the Technique "Exploit Public-Facing" and Tactics "Initial Access." As per the “2019 State of the Internet/Security” report [1] by Akamai, SQL injection attacks account for 77% of all application attacks in 2019. SQL injection exploits add additional SQL query to the legitimate SQL query. This addition of exploitable SQL query to the legitimate SQL query lays the foundation of the query integrity algorithm to detect SQL injection by instrumenting web applications. The blog details the algorithm followed by the results of the algorithm to detect exploits generated by sqlmap[4] tool. In the last section, we conclude by sharing the inherent advantages of using the algorithm over other methodology.
Technical Details
Figure 1.0 is an example of code that is vulnerable to SQL injection attack. The code accepts the username from the HTTP request in the variable user. This variable user then acts as an input to the SQL query sqlStmt. In the subsequent part of the code, the query gets executed by the function Connection.Execute().
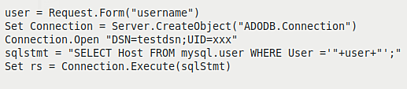
Figure 1.0 Code Vulnerable to SQL Injection “SELECT Host FROM mysql.user WHERE User =‘bob’;”, is an example of the legitimate SQL query executed by the application. The legitimate query sent to the database is defined in the application and the value of the variable user as ‘bob’ is taken from the value field of the methods which accept user input such as the GET, POST, etc.. Figure 2.0 shows the PostgreSQL parse tree of the normalized query.
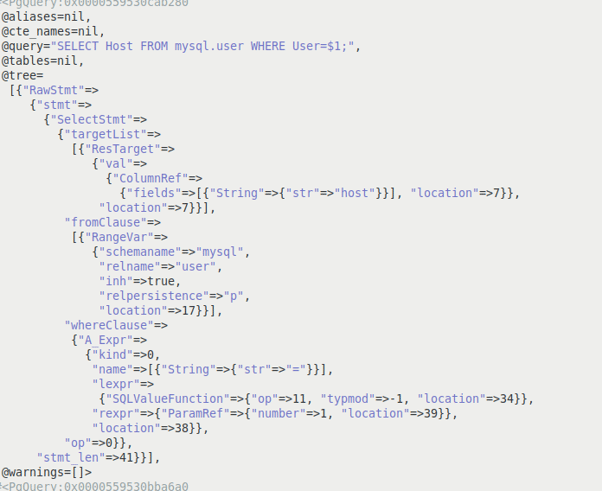
Figure 2.0 PostgreSQL parsetree of the valid normalized Query In the case of an SQL injection exploitation, a threat actor will insert malicious SQL clause along with a value into the methods that accept user or external inputs (such as GET, POST). This malicious clause will get executed by the application along with the legitimate query. Explaining it with the example, if the threat actor injects malicious SQL clause “UNION SELECT username, Password FROM Users”, by appending it to the value of the variable user “bob”, the query that gets executed by the application becomes “SELECT Host FROM mysql.user WHERE user= ‘bob’ UNION SELECT username, Password FROM Users ;” A PostgreSQL parse tree of the normalized SQL query with the injected SQL clause “UNION SELECT username, Password FROM Users” is shown in Figure 3.0. As can be seen in Figure 3.0 an additional node is created in the PostgreSQL parse tree as a result of the inserted SQL clause.
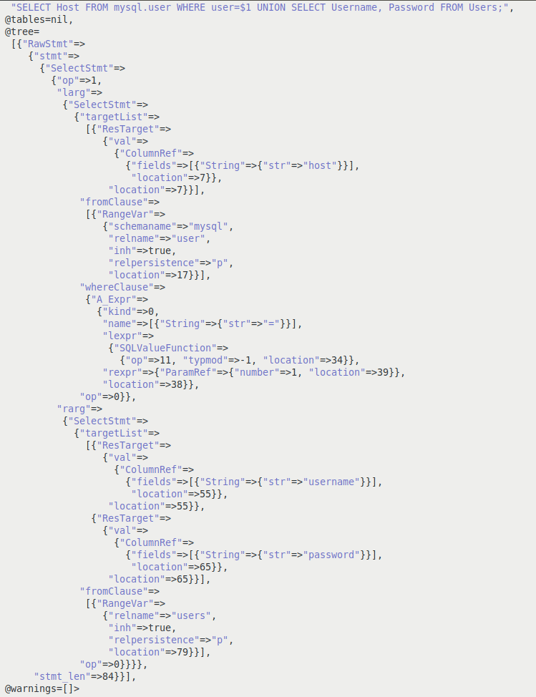
Figure 3.0 PostgreSQL parse tree with the Injected SQL command SQL injection exploits will introduce an additional SQL clause to the database. This injected exploit SQL clause will be reflected as an extra or deleted nodes in the query parse tree of the legitimate normalized SQL query.
Detection of SQL injection Exploitation
The algorithm to detect the SQL injection attack makes use of the application-level hooks to construct a program dependency graph (PDG). The PDG captures the flow of data and control from methods which accept external or user input such as GET, POST, Cookies etc. to the functions which execute the SQL query such as mysql_query(), mysql_db_query(), mysql_unbuffered_query(), pg_execute(), pg_query(), pg_query_params(), pg_prepare(), pg_send_query(),and pg_send_query_params(). Once the PDG is generated, it is used to identify the legitimate SQL queries which are the sink for the value from the methods which accepts user’s or external input such as GET, POST etc. These SQL queries are the parameters for the SQL query execution functions and are stored as the parse tree. Any injected malicious SQL clause by a threat actor to the legitimate SQL query will get reflected by the additional or deleted node in the parse tree of the normalized legitimate SQL query. For every database access, the parse tree of the executing query is compared with the parse tree of the legitimate query. If there is any additional or deleted node in the parse tree of the executing SQL query, then it gets matched with the value or with the part of the value passed to the methods that accept user or external input such as GET, POST etc. In the case of a match, an alert for SQL injection is raised.
sqlmap is an open-source penetration testing tool that can be used to stream boolean-based, blind, time-based blind, UNION query-based, stacked queries, and out of band SQL injection exploits. The query integrity algorithm successfully detects the variation of exploitable exploits generated by the SQL Map tool.
Conclusion
The algorithm to detect the injection based exploitation has the following inherent advantage:
- The algorithm identifies the injection vulnerability in the code during the invocation of the SQL query execution functions. With each detected exploitation attempt by a threat actor, the vulnerable code path automatically gets detected. This automatic identification of the vulnerable part of the code will aid to patch the code preventing further exploitation.
- The algorithm only leverages binary instrumentation of the application to detect injection- based exploitation. Hence the detection is independent of the deployment of an application and the manner it accepts external inputs. The application can be deployed as a backend microservices and can accept batched requests which get broken down by the middle layer and served to the rear end microservices. In this scenario also the algorithm will detect injection exploits.
- Traditionally WAF has been used to detect web application exploits. Detections of exploits over the HTTP traffic are prone to evasion[3]. The query integrity algorithm detects exploitation during the execution of the query; it is immune to the evasions applicable to the network packet processing layer.
- The algorithm raises an alert during the actual exploitation. It is independent of the type of the application and the operating system on which the application is executing. Hence the algorithm is capable of detecting both known and zero-day vulnerabilities in the application.
These advantages makes query integrity algorithm recommended solution to prevent SQL injection exploitation.
References [1] 2019 State of the Internet / Security (Volume 5 issue 6): 2019 — A Year in Review, https://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/soti-security-a-year-in-review-report-2019.pdf [2] Exploit Public Facing Application, https://attack.mitre.org/techniques/T1190/ [3] Evasion in Intrusion Prevention /Detection System. https://www.virusbulletin.com/virusbulletin/2010/04/evasions-intrusion-prevention-detection-systems [4] SQL injection tool http://sqlmap.org
